Mounting encrypted LUKS kingston pendrive on macos
TLDR 😄
If you read the previous post you should already know I switched from linux to macos. And I learned a new thing! Back in the day I bought a barely used 8GB Kingston Data Traveler (DT) 2000, very cheaply, to keep my most important files safe and portable. It comes with the build-in keypad, you type your password, plug the stick in and it just works, you can now access you files. It’ll wipe your data if you fail to type your password 10 times. I used it for a while, but was bothered by a thought. Would you trust Kingston or any other company with a device they consider secure which you can’t even update and their soft isn’t open-source? Probably yes, because you’re not Snowden 😛 Should be more than enough to keep you files hidden from your grandmother! Btw, don’t underestimate your granny 😄 It wasn’t enough for my brain though, it was still poking me every now and then, annoying! In the end, I wiped the whole pendrive and encrypted it. I don’t remember what I used, probably something which was available via my gui (did I use Ubuntu back in the day?? 😱). I imagine it could be some kind of encrypt checkbox. Fancy encryption FTW. It was enough for my brain to let go 😄 Today, I faced a small issue. I realized that LUKS is not supported by macos. They probably have their own secure tools, which I think I trust even less than the Kingston hardware-based, Full Disk AES 256-bit data encryption in XTS mode. Fancy marketing. Anyway, I already have encrypted partition inside a hardware encrypted USB stick, and the issue, I can’t access my data on macos. Googling time!
I stumbled upon some very neat tool called linsk:
Linsk is a utility that allows you to access Linux-native file system infrastructure, including LVM and LUKS on Windows and macOS.
I decided to give it a go. I followed the install manual, added missing qemu and golang as described in the readme and, finally, linsk itself. Time for the macos manual. Oh, and don’t forget to add golang bin folder to your shell PATH.
- Build
linsk build
- Connect the encrypted usb stick, macos will show a waring alert box to ask if you want to mount it. Don’t do that! Hit
ignore. You can read console warning for more info later
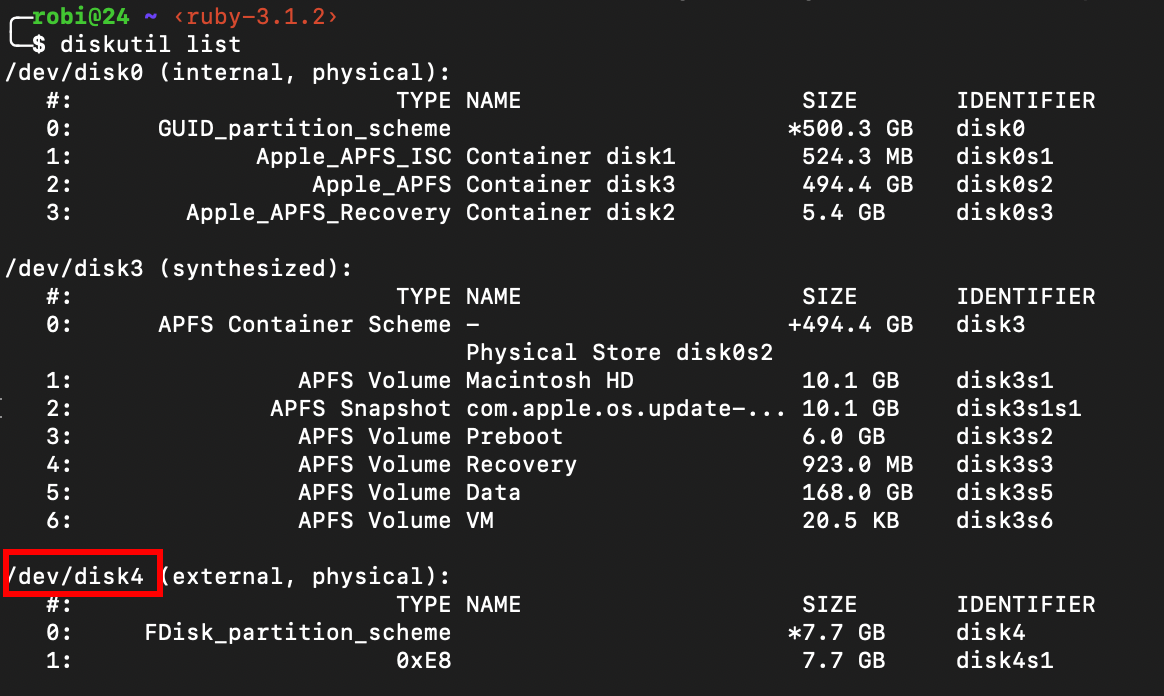
- Run the below command to find the path. In my case it’s
dev:/dev/disk4
diskutil list
- Next we list what’s inside the
disk4
sudo linsk ls dev:/dev/disk4
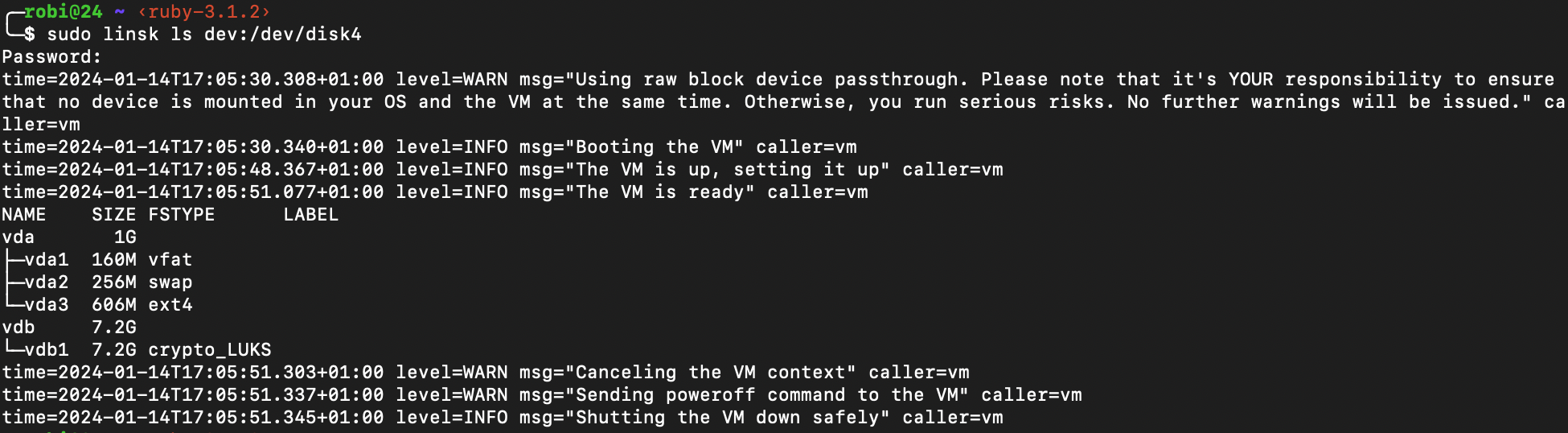
And yes, you’ll be prompted again. Annoying, but we can live with it. As you can see it says crypto_LUKS which means the whole pendrive is behind our encryption wall. It’s mentioned under advanced section.
- We need to run
lson ourvdb1with the--luks-containerflag
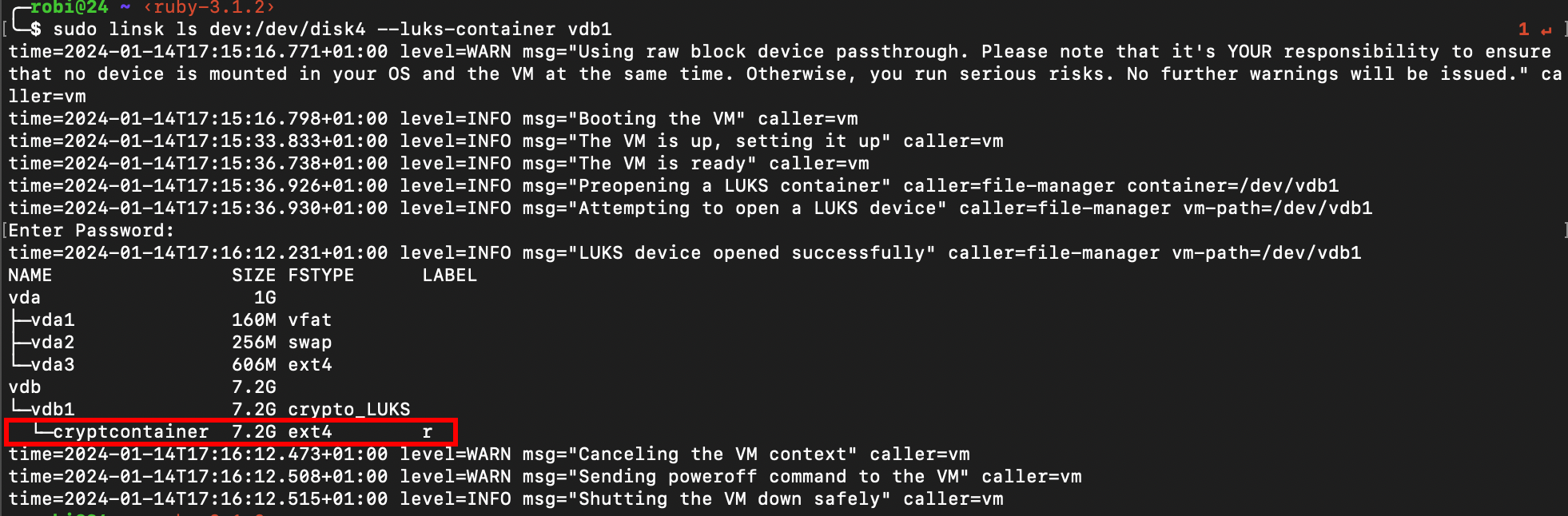
So close, we can see the cryptcontainer, the file system and r, probably read flag.
- Run! In the docs you find a magic
mapperkeyword in command examples. I expect this is what we need to add to our last parameter which iscryptcontainer?
sudo linsk run dev:/dev/disk4 --luks-container vdb1 mapper/cryptcontainer
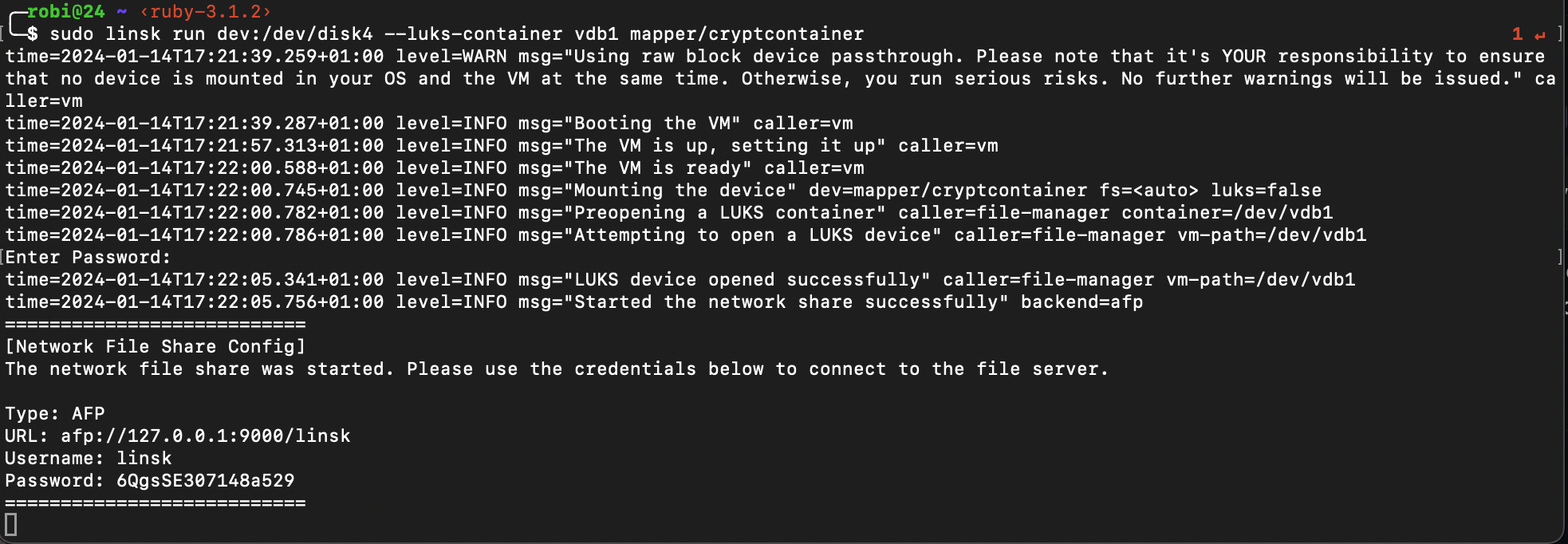
That’s it! Of course after you successfully typed three passwords, first on the stick, second for sudo and third one for your encrypted vdb. And you guessed correctly, I also encrypted few files separately, so it would be 4! 🤯
linsk hosts the AFP server for you. This is the bridge between linux and macos we needed.
- Now, open this
Finderand hitGo -> Connect to server
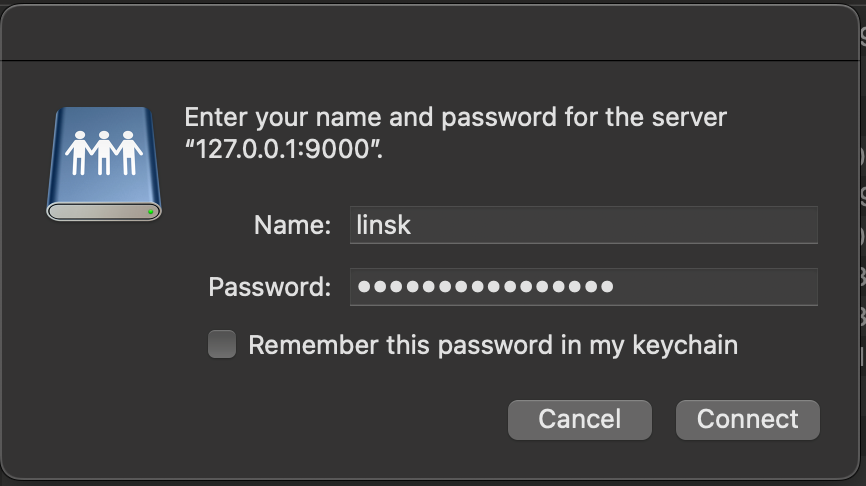
- Enjoy!
Ahh, and the last one. Don’t forget to safely unmount the drive! I got an led which flashes during the save/read process. I suppose you don’t want to break some bytes, especially, during the save process on double encrypted drive ☠️
TLDR
Install luks, it’s a small VM which hosts an AFP server to access your files. Ignore all macos warnings.
diskutil list # to grab the disk number
sudo linsk run dev:/dev/disk4 --luks-container vdb1 mapper/cryptcontainer # replace disk4 with your disk number
# command + K to open finder